Pinned Tweet

34
18
246






 Webinar Alert
Webinar Alert
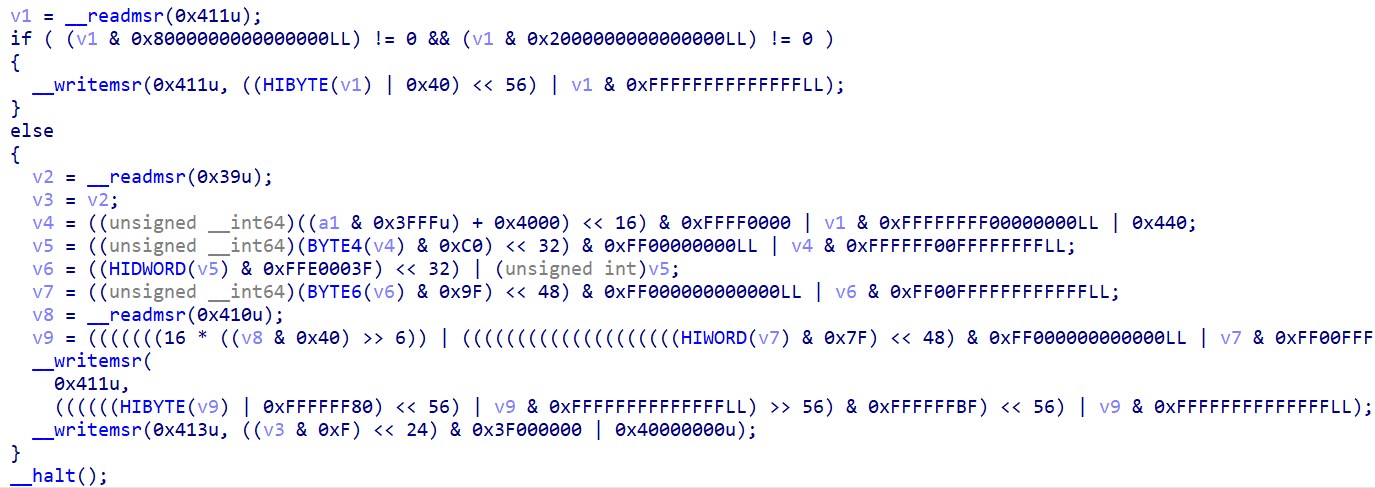
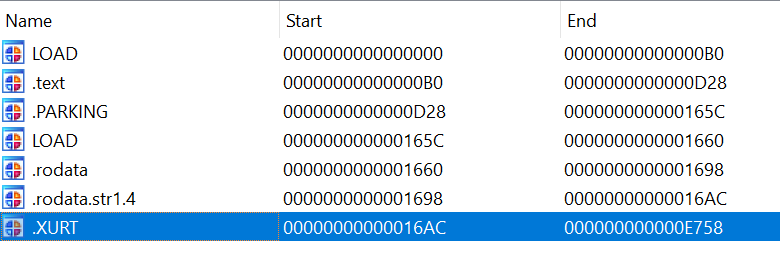
 In spring of 2021, @kaspersky researchers identified a novel threat against UEFI in the wild - a benign #UEFI #firmware image named as Moonbounce
In spring of 2021, @kaspersky researchers identified a novel threat against UEFI in the wild - a benign #UEFI #firmware image named as Moonbounce
 Find out in-depth about Moonbounce with Mark @_marklech_
Register now
Find out in-depth about Moonbounce with Mark @_marklech_
Register now bit.ly/3HeVozt
#hardwear_io
bit.ly/3HeVozt
#hardwear_io








 securelist.com/moonbounce-the
securelist.com/moonbounce-the securelist.com/moonbounce-the
securelist.com/moonbounce-the