Crypto mixers, nested exchanges, cash-out, intermediary crypto wallets, DeFi, darkweb laundering services...
How cybercriminals launder dirty crypto and what this means for #ransomware victims 👉 kas.pr/y6zw
Eugene Kaspersky

@e_kaspersky
Eugene Kaspersky’s Tweets
Microkernel OS vs Monolithic kernel OS. What's better and which one will hold the future? 👉 kas.pr/f782

1
4
19
What day today?
It's Anti-Ransomware Day!
We look back on the events that shaped the ransomware landscape in 2022, review the trends that were predicted last year, discuss emerging trends, and make a forecast for the immediate future 👉 kas.pr/p8v1

6
20
Deepfakes are now a huge darknet industry.
We made a deep dive to the darknet forums to study this underground market using Kaspersky Digital Footprint Intelligence service, and here are the findings 👉 kas.pr/9bmk

2
5
12
Kinoko No Yama, Takenoko No Sato, Umaibou Cheese Flavour and Jagarico Wasabi Soy Sauce - just a few of the popular Japanese snacks tried on his recent trip to #Japan.
Check it out ⇒ youtu.be/WhXzzJqhn1g #Snacks #Tourism
4
5
In its February update, Microsoft buried Internet Explorer once and for all. Or did it?
We investigate what really happened 👉 kas.pr/er4h

8
15
A few useful tips on how to choose an alternative to Google Chrome that take data privacy more seriously 👉 kas.pr/4yom

4
8
15
We are proud to share that the last decade has seen our products stand the test of time and ace over 800 independent reviews.
With 587 first places🥇 and 685 top-3 finishes🥉in these tests, our solutions are trusted by millions worldwide🌍
Details 👉 kas.pr/r86q

1
7
Hi all – from Everest Base Camp! 5364 meters above sea-level! But that’s enough for me – we weren’t planning on going further anyway :)


6
8
47
Jocker, Harly, now Fleckpe
Not quite an Easter egg: a new family of Trojan subscribers on Google Play 👉 kas.pr/6h2q

3
8
I love it when people have fun at work. Sadly, I was back at JP office when tried these snacks, but is definitely worth the watch for his reactions to Japanese snacks -
3
6
The bars serve the drink Nepenthe, which is a lubricant for protection against mechanical wear-and-tear mixed with subparticles delivering programming updates.
Truth be told, this doesn’t seem very safe. Still, at least now we know they can get any updates at all!
1
Show this thread
BTW, we now know how droids get their software updates.
It turns out, they visit bars to get updated… through booze! (I guess that makes a good excuse when asked “why are you drunk again?”: “Just updating, darling!”)
1
2
5
Show this thread
JICYMI:
#Cybersecurity in Mandalorian, S01: kaspersky.com/blog/star-wars
#Cybersecurity in Mandalorian, S02:
1
3
Show this thread
MTFBWY Earthling!
On May 4 we always review the status of #cybersecurity in a galaxy far, far away.
Today: Cybersecurity in season 3 of The Mandalorian 👉 kas.pr/n5wc

2
6
15
Show this thread
Enhance your network security and stay ahead of the ever-evolving threat landscape with Kaspersky xTraining's Suricata for Incident Response and Threat Hunting course. #networksecurity #training #suricata
👉 kas.pr/9gmi
1
5
Join , Dmitry Galov and as they look at #ransomware trends for 2023. Included in the webinar:
✔️ 2022 ransomware overview
✔️ Updated TTPs
✔️ Target types gangs are after
✔️ How to protect your systems
Learn more ⇒ kas.pr/81u6

3
11
Fake accounts on LinkedIn: time for a purge!
Why you should purge your company’s LinkedIn page from fake employee profiles, and how to do it
👉 kas.pr/19sq

1
6
12
How good #ChatGPT recognizes malicious URL?
We conducted an experiment:
DR: 87.2% / 93.8%
FPR: 23.2% / 64.3%
For a 0-shot system it's amazing. But it has limitations for #cybersecurity due to “hallucination” tendency and limited context window 👉 kas.pr/zkt2

2
38
73
We recently released a new version of Security & VPN for complete protection of #Android devices.
An overview of new features and updates 👉 kas.pr/bf6b

1
3
12
What is Conversation Hijacking and how to deal with it?
Cybercriminals can access the e-mails of folks you’re in correspondence with and then try to hijack your conversations 👉 kas.pr/ew2x

6
9
ICYMI - Vulnerabilities have been found in iOS & macOS. The flaws include one which allows attackers to gain access to sensitive user info by intercepting net traffic, as well as a bug that allows malware to bypass Apple's security & gain root access.
3
8
The deepest mine in Europe?
It's in the town of Gui (pronounced Guy; not Gay) not far from Orenburg.
Guess what I just did the other week? 👉 kas.pr/446j




3
2
12
How AI can leak your private data?
Image-generating neural networks like DALL-E, Imagen or Stable Diffusion are already everywhere.
Put aside the ethics and legality of generative art let's discuss what privacy risks do they pose? 👉 kas.pr/me77

3
10
17
We tracked #Tomiris APT over 3 new attack campaigns in 2021-2023, and our telemetry allowed us to shed light on the group.
and share our findings with the community, and discuss further evidence of a connection to #Turla 👉 kas.pr/c7zd

1
14
19
Amazing news! 🏆
AV-TEST has confirmed that Kaspersky's Endpoint Security for Business, Small Office Security, and Internet Security have all proven to be 100% effective against ransomware attacks!!

9
17
5 types of attacks on hardware crypto wallets
Hardware crypto wallets are effective at protecting your cryptocurrency, but they can still be stolen from.
Let’s address the risks their owners need to be protected from 👉 kas.pr/s15x

2
8
28
Introducing our fastest #VPN yet! Powered by the #WireGuard protocol and Hydra servers. Enjoy lightning-fast speeds and enhanced security features, including #malware blocking and data encryption as standard.
Learn more 👇
1
9
18
We detected a significant increase in attacks with QBot Trojan using e-mail messages based on real business letters. This afforded the attackers the opportunity to join the correspondence thread with messages of their own 👉 kas.pr/dt8h


2
6
14
As many groups are using common TTPs, #ransomware is now becoming a RaaS model. #Kaspersky's next #webinar features👇
✔️Insights from many RaaS operations
✔️ stats on ransomware evolution & TTPs
✔️Attack workflow via MITRE ATT&CK
Register now👇 bit.ly/43y8aVu

9
14
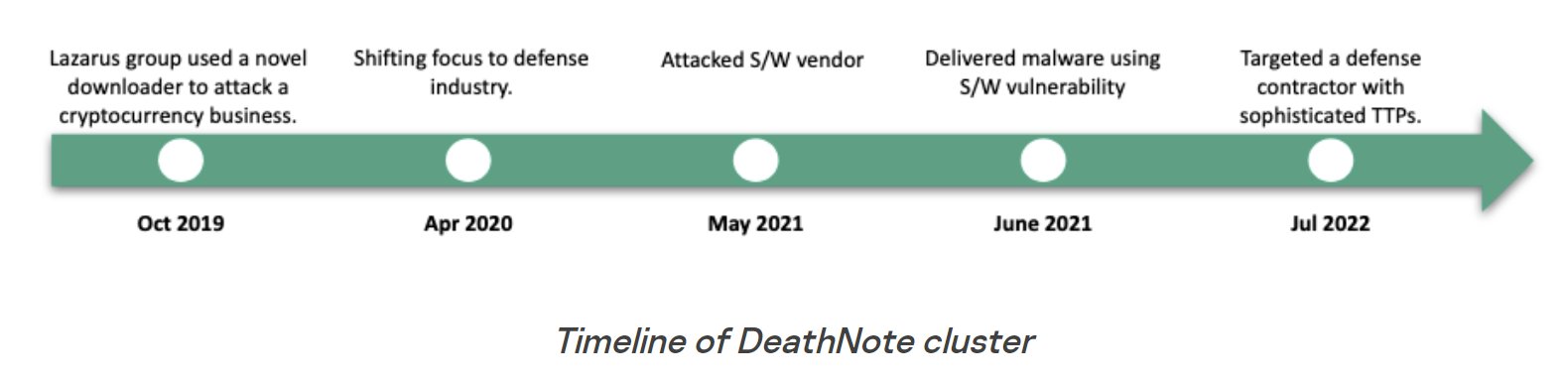
The #Lazarus group has multiple sub-campaigns. We have previously published information about the connections of each cluster of this group.
A new addition to this research is a detailed analysis of an active cluster dubbed DeathNote.
👉 kas.pr/ns42



2
26
58
In Feb 2023, Kaspersky proactive detection technologies discovered exploits similar to CLFS.
Further research revealed a zero-day vuln in Windows (incl W11) used by a sophisticated #ransomware group.
Further details on #Nokoyawa attacks 👉 kas.pr/p74e by


1
13
20
Overview of Google Play threats sold on the dark web.
Highlights:
✅ Loader for app delivery to Google Play = $2-20K
✅ Cryptocurrency trackers most often hide malware
Details 👉 kas.pr/v7fa

1
8
18
What really goes on when your device is in repair?
Informally servicemen admit they occasionally held viewings of homemade porn found on the devices they repair.
How to protect yourself from nosy maintenance technicians? 👉 kas.pr/z5uj

5
10
Hey everyone, this is my first tweet! We identified a backdoor we dubbed #Gopuram, the final payload in the #3CX attack. The threat actor (likely to be Lazarus) has deployed it to cryptocurrency companies. More details in this thread and on Securelist (securelist.com/gopuram-backdo)
8
111
177
Show this thread
An excellent guide from that identifies the benefits and drawbacks of using an #MSSP and provides guidance for #organizations looking to choose one👇
#business #threatintelligence #SOC #cybersecurity #InfoSec
8
14


















