You can now filter by repository topic or team on the organization-level Dependabot, code scanning, and secret scanning pages in security overview.

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
You can now filter by repository topic or team on the organization-level Dependabot, code scanning, and secret scanning pages in security overview.

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
GitHub Advanced Security users can now view alert metrics for custom patterns at the repository, organization, and enterprise levels directly from the custom pattern's page. Custom patterns with push protection enabled also show metrics like total secrets blocked and bypassed.
We welcome feedback in our code security discussion.

In July 2022 the public npm registry migrated away from the existing PGP signatures to a new ECDSA signatures for signature verification.
PGP based registry signatures will be deprecated on April 25th 2023. This means no new packages will be signed with PGP keys from this date onwards and the public key hosted on Keybase will expire.
Read more about registry signatures.
You can now programmatically view and act on repository advisories via a new REST API. New endpoints to create, view, list, and update advisories are available to all. Additionally, new webhooks have been introduced that will alert maintainers when advisories are published or when a private vulnerability report is submitted.
Current advisory permissions extend to API usage.
GitHub enterprise and organization owners can now use a REST API to delete their organizations and all corresponding repositories. Organization names will be locked for 90 days following the organization deletion.
We recommend reading our Terms of Service around account deletion before utilizing this endpoint.
To learn more, please read our Organization REST API documentation.
GitHub Enterprise Cloud administrators may need to review external identity information via the GraphQL API. Historically, this has required a token with the admin:org or admin:enterprise scope. We've taken a "least privilege" mindset in reviewing this flow and have now made this information available via the read:enterprise and read:org scopes for enterprise owner and organization owner actors.
For more information, see the GraphQL API documentation for Enterprise and Organization SAMLIdentity objects.
We now show bypassed branch protection rules in response to Git pushes. These are information messages and are not designed to block workflows.
Historically there was no indication after a Git push that branch rules had been bypassed.
Repo admins, actors with the bypass branch protections permissions, and actors in bypass lists on branch protections will now see a list of rules that were bypassed.

We appreciate your feedback in GitHub's public feedback discussions
The dependency graph shows a summary of the manifest and lock files stored in a repository. The repository view has an updated user experience that includes:
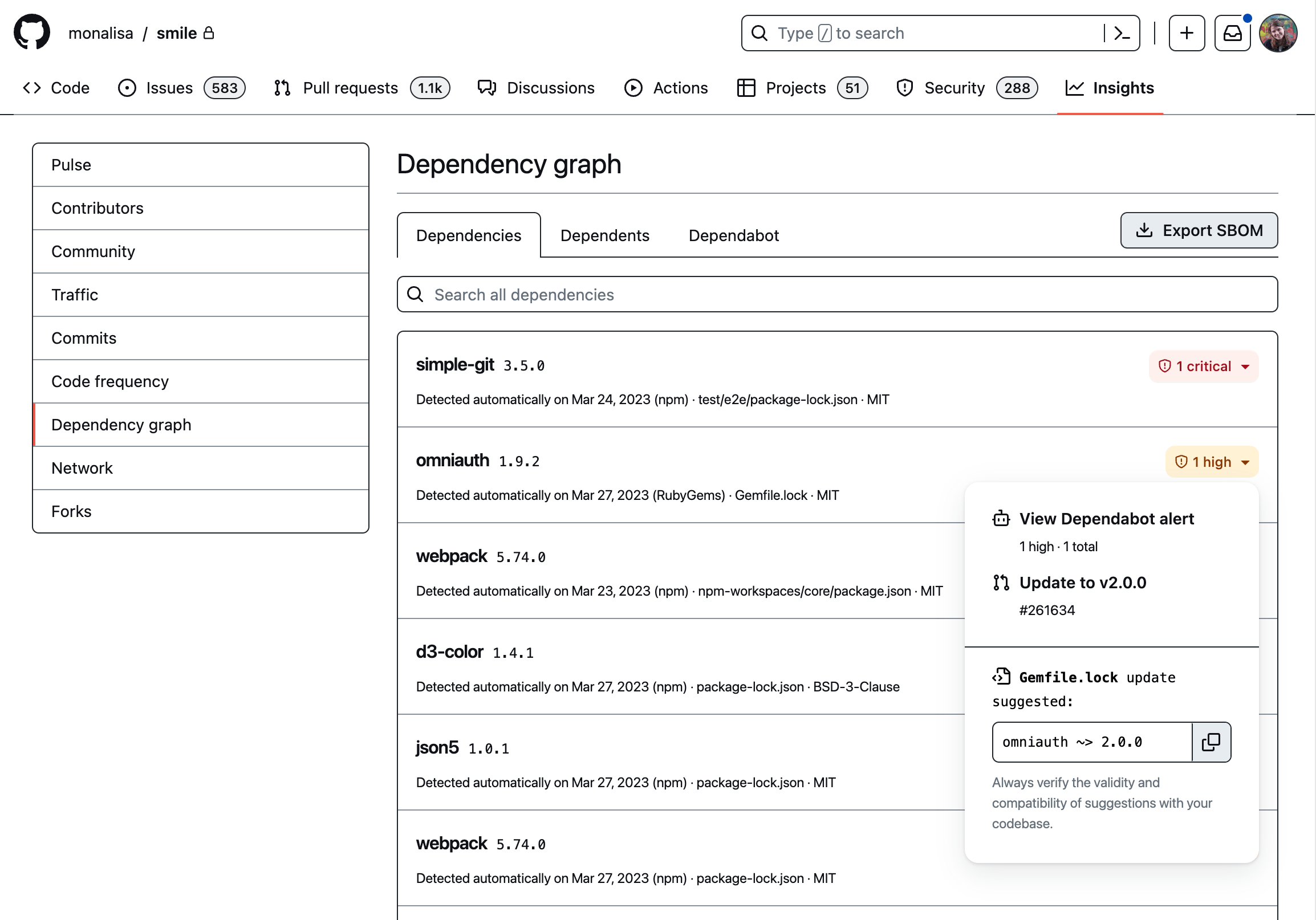
Access a repository's dependency graph from Insights > Dependency graph.
A software bill of materials (SBOM) is a standardized inventory of a software project's dependencies and associated metadata (versions, licenses, etc). You can now export your repository's dependency graph as an SBOM adhering to the SPDX 2.3 specification.
Click "Export SBOM" on a repository's dependency graph to generate an SBOM representing the head of the main branch. The resulting JSON file will download in your browser. Exporting an SBOM is free for all cloud repositories on GitHub, and can be performed by anyone with read access to a repository.
A supporting REST API to generate SBOMs for repositories will be available in the coming weeks.

The GitHub Actions extension for VS Code is now in public beta. This extension includes rich editing features, such as syntax validation and autocomplete, making workflow authoring and editing faster and easier. Developers will also be able to view workflow runs, inspect logs, and trigger re-runs directly from VS Code.
To get started, visit the VS Code Marketplace or learn more about the extension's capabilities from the Actions VS Code Extension blog post.
See what's next for Actions by visiting our public roadmap.
The new code scanning tool status page allows users to view the status of CodeQL and other code scanning tools.
The page shows all the tools that are enabled on the repository and provides information about their setup types, configurations, and any relevant failures or warnings. If a tool is not working as expected, this is a good place to start troubleshooting the issue.
You can visit the new tool status page by using the button at the top of the repository's Code Scanning page.

The page indicates three possible statuses for the tool: all configurations are working, some need attention, and some are not working.
Code scanning needs to have received at least one analysis for the default branch to provide a tool status. Only the status of the default branch is reported.
The page shows the latest state of all analysis configurations for the tool. For instance, if you created two separate workflows to scan two distinct parts of the repository independently, the page displays the most recent state of the tool by combining the statuses of both.
For each tool, the page provides actionable information about misconfigurations and errors, the number of scanned files per language, the setup types and configurations, the list of rules the tool checks against, and detailed CSV reports.

To help you with debugging, the tool status page shows error messages gathered from multiple code scanning system components during tool setup and analysis execution. These include errors from CodeQL, code scanning workflows, SARIF upload limits, and the internal code scanning system.
Third party code scanning tools are not yet able to deliver tool related errors to the page. In the future, these tools will be able to submit error messages to code scanning via SARIF uploads.
A Scanned Files section shows the number of analysed files per language compared to the number of files in the repository.
The section helps you determine whether code scanning tools are operating correctly on your repository and only shows information about languages supported and analysed by the tool while ignoring languages that are present in the repository but are not supported or being analysed by the tool.
This section is not yet displayed for third party code scanning tools. In the future, third party tools will be able to submit error messages to code scanning via SARIF uploads.
This has shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
Learn more about code scanning and the tool status page.
Learn more about GitHub Advanced Security.

We improved the color contrast of our default light and dark themes on github.com, making them accessible to all users. These changes were made to Primer, GitHub's Design System, as part of our commitment to making GitHub inclusive to all developers. Visit accessibility.github.com for more information.
The VS Code light and dark themes will also be updated to match these changes.
Educators using GitHub Classroom can now optionally set a assignment deadline to be a "hard cutoff." If you use a cutoff date, students will lose write access to their assignment repositories after the cutoff date has passed.
You can grant individual students and groups extensions to allow them more time to submit an assignment.
The assignment dashboard view is now updated to better indicate whether a student has committed to their repository on-time (before the deadline), late (after the deadline), or both. You can easily filter the dashboard view on these states, and quickly click through to the latest on-time and late commits of a student's repository.
Addressing a big ask from students, they can now click a button in their assignment README to view the deadline of the assignment at any time.
Read more about creating a new assignment, extending a deadline, and students' ability to view their assignment's deadline.
We've recently released a few improvements to the slide-out enablement panel on the security coverage page in security overview:

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
Learn more security overview and send us your feedback
Learn more about GitHub Advanced Security
The repository dependency graph GraphQL API preview now returns dependencies that have been submitted using the dependency submission API.
Organization owners can now automate the approval and auditing of fine-grained personal access tokens (PATs) in their organization using a GitHub app. New APIs and webhook events allow a GitHub app to be notified of new PAT requests in an organization, review the request, and then approve or deny the PAT. They also provide a view of all approved fine-grained PATs for an organization, with the ability to revoke their authorization as well. These APIs and events are part of the ongoing fine-grained PAT public beta that launched last year.

Details included in the webhook event and API listings include the repositories and permissions requested, the expiration time of the token, and the user's explanation for what they plan to do with the PAT. The personal_access_token_request events are generated when a request is created, approved or denied by an administrator or application, or cancelled by the requesting user.
Only a GitHub app is able to call these APIs, either acting on its own or on behalf of a signed-in organization administrator.
The organization_personal_access_tokens permission is needed to manage the active tokens, while the organization_personal_access_token_requests permission enables the app to recieve webhooks about requests and call the request management APIs.
Organizations must have the personal access token approval flow enabled in order to manage these requests, otherwise fine-grained personal access tokens are automatically approved for the organization (which generates a personal_access_token_request: approved event).
To learn more about these APIs, see "List requests to access organization resources with fine-grained PATs" and the "personal_access_token_request webhook event". To learn more about fine-grained PATs, and how to enable them for your organization, see "Setting a personal access token policy for your organization".
If you have feedback or bugs to report about fine-grained PATs, please let us know in the dedicated feedback discussion.
Enabling caching by default has demonstrated improved workflow performance, and can reduce build times by 20-40% for repositories with dependencies greater than 100 MB! This change has been made to the latest setup-go Action(V4). Developers no longer have to specify the cache: true parameter in their YAML file to obtain the benefits of caching. For more information on building, testing, and caching dependencies with Go, check out the docs here!
In addition to Ubuntu & Windows, GitHub Actions now attaches a SBOM (Software Bill of Materials) to hosted runner image releases for macOS. In the context of GitHub Actions hosted runners, an SBOM details the software pre-installed on the virtual machine that is running your Actions workflows. This is useful in the situation where there is a vulnerability detected, you will be able to quickly tell if you are affected or not. If you are building artifacts, you can include this SBOM in your bill of materials for a comprehensive list of everything that went into creating your software.
To check out the new files, head over to the runner-images repository release page now or check out our docs for more information.
We're thrilled to introduce the GitHub Classroom CLI extension for the GitHub CLI, designed to simplify the lives of teachers everywhere. With this powerful new tooling, teachers can create their own personalized workflows, as well as streamline any custom solutions they've already built.
To get started, ensure you have the GitHub CLI installed, then install the extension with the following command:
gh extension install github/gh-classroom
The GitHub Classroom CLI extension provides a suite of commands to help you navigate your classrooms and assignments with ease. Here's a quick overview of its capabilities:
gh classroom list: List all your unarchived classroomsgh classroom view: Show the details of a classroom, such as its name, description, URL, and rostergh classroom assignments: Display a list of assignments for a classroomgh classroom assignment: Show the details of an assignment, such as its title, type, deadline, starter code URL, and number of submissionsgh classroom accepted-assignments: List your students' accepted assignmentsgh classroom clone starter-repo: Clone the starter code for an assignmentgh classroom clone student-repos: Clone all your students' submissions for an assignment (a scriptable alternative to the Classroom Assistant desktop application)To target a specific classroom, use the -c flag with each subcommand (retrieve a classroom's ID through selecting it in gh classroom ls or gh classroom view). In the absence of the -c flag, an interactive picker navigable with arrow keys will help you select the target classroom.
This collections of subcommands marks the beginning of our journey to deliver power features that save you time and enhance your workflows.
You can report issues or request features on our public repository, where we look forward to open sourcing the code in the coming weeks.
Share what you build with the GitHub Classroom CLI in our Global Campus for Teachers Discussions forum!
GitHub Security was notified about an issue where private issue and pull request titles would be displayed in search results. Our Security team investigated potential instances and determined that this only occurred when the author of the commit was authorized to view the issue or pull request and the commit was titled as a link to the private issue or pull request. Additionally, this only happened while using the new code search (beta). This issue was introduced when the new code search (beta) launched and was fixed on January 17, 2023. As this issue has been addressed, there is no further action that is required by any user.