Blog
Stay up to date on company and partner news, product tips, and industry trends.


Jan 12, 2023
Forging ahead: A CISOs top recommendations to stay secure in 2023
Last year, we anticipated that 2022 would be challenging for cybersecurity. This was proven true with the countless number of sophisticated high-profile phishing and ransomware attacks like DropBox, Twitter, Rockstar Games and Uber (twice). With the introduction of phishing-as-a-service and other sophisticated toolkits that target weaker forms of 2FA, security teams are now prioritizing phishing …
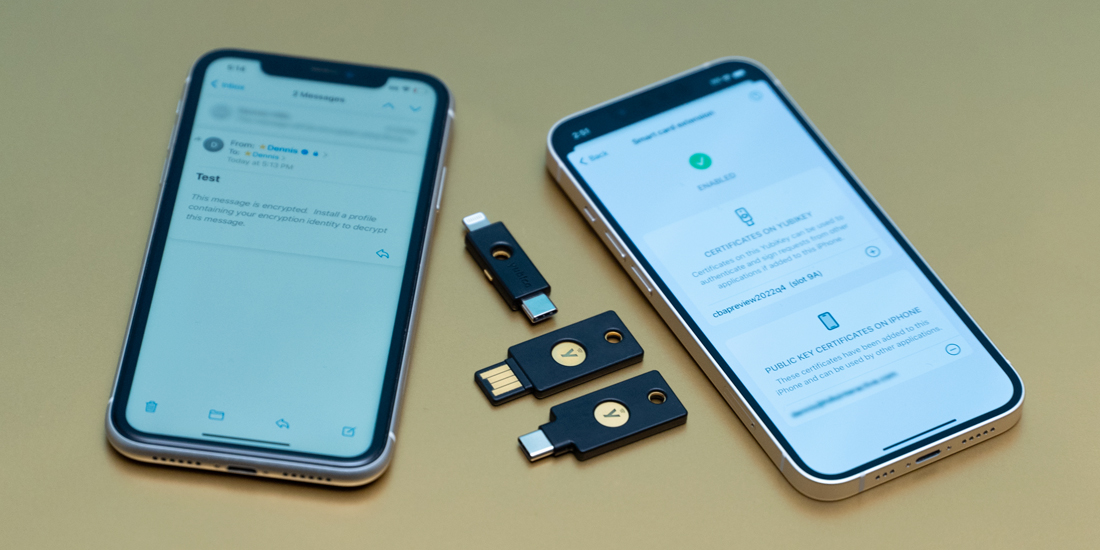
Dec 22, 2022
Uncovered PIV use cases on iOS: Using YubiKey as a smart card on iOS
In a recent post we discussed the concept of using a YubiKey as a smart card on iOS. Now that we’ve outlined the overall concept, we’d like to expand by exploring the unlocked use cases for using a smart card for authentication, creating digital signatures, and decrypting messages and documents on Apple iPhones and iPads. …

Dec 21, 2022
2022: A year of phishing with a solution to calm the seas
In 2022, phishing scams continued to hook into consumers and enterprise accounts. In fact, recent research from EMA revealed that 87% of surveyed businesses indicate that their organization experienced an identity-related security breach in the preceding 12 months. Many successes of the sophisticated phishing scams were due to legacy MFA implementations such as SMS, mobile …

Dec 15, 2022
Apple announces upcoming support for security keys: A look at the past, present and future of Advanced Protection with YubiKeys
In 2022, if one thing has been proven, it has been made very clear that not all multi-factor authentication (MFA) is created equal. Vulnerabilities with legacy forms of MFA, such as SMS, TOTPs, and mobile-based apps, continue to be the target and victims of data breaches, with attackers taking aim in record numbers in 2022. …

Dec 13, 2022
An inside look: How hackers rely on low effort tactics for phishing attack success
Phishing continues to make headlines with attackers using stolen credentials to gain access to valuable systems and sensitive data. Although phishing has been a known technique for a long time, the industry is still struggling to effectively defend against it. This may seem surprising to many as “phishing” calls to mind poorly written emails, generic …

Dec 7, 2022
Survey results are in: 59% of employees still rely on username and password as primary method to authenticate their accounts
Our inaugural State of Global Enterprise Authentication Survey – which we exclusively previewed in September during YubiSummit – captures a snapshot of how companies around the world are tackling authentication. We received over 16,000 responses from entry-level employees up to business owners at organizations ranging in size from one to 2,000+ employees, in eight countries: …

Dec 1, 2022
The Key to election security: Q&A with Michael Kaiser, president and CEO of Defending Digital Campaigns
The election ecosystem is a prime target for cybersecurity threats and the 2022 United States Midterm election cycle has been no different. Though many security improvements have been made in recent years, bad actors continue to become more sophisticated in gaining access to private information – often driven by phishing attacks. Officials in charge of …



