OSINT Framework: The Perfect Cybersecurity Intel Gathering Tool
Reading time: 6 minutesIntel and reconnaissance are among the first steps taken in any cybersecurity research effort, and as we've seen in our previous post, OSINT plays a big role in data collection. So what is OSINT?
While there are tons of public resources for getting information about any individual or organization, they are spread throughout different parts of the internet, sometimes mixed with security tools and data intelligence utilities. That's why the OSINT Framework plays such an important role.
Today we will explore what the OSINT Framework is, its main objective, and the most useful resources you can find within.
What is OSINT Framework?
OSINT Framework, as its name implies, is a cybersecurity framework, a collection of OSINT tools to make your intel and data collection tasks easier.
This tool is mostly used by security researchers and penetration testers for digital footprinting, OSINT research, intelligence gathering, and reconnaissance.
It provides a simple web-based interface that allows you to browse different OSINT tools filtered by categories.
It also provides an excellent classification of all existing intel sources, making it a great resource for knowing what infosec areas you are neglecting to explore, or what will be the next suggested OSINT steps for your investigation.
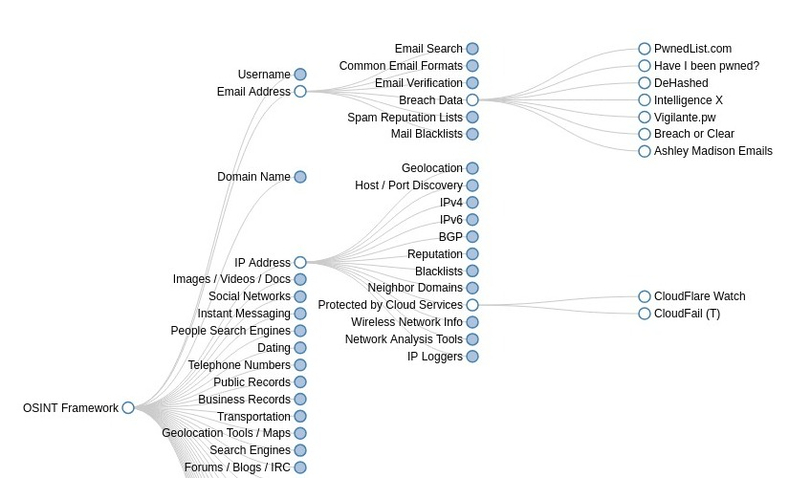
OSINT Framework is classified based on different topics and goals. This can be easily seen while taking a look at the OSINT tree available through the web interface.
OSINT Framework classification
When you immediately load the website https://www.osintframework.com you'll notice the OSINT tree is before your eyes on the left side of your screen.
There are some highlights you should know; take a look at the following indicators on the right side, for some of the listed tools:
- (T) – Indicates a link to a tool that must be installed and run locally
- (D) – Google Dork (aka Google Hacking)
- (R) – Requires registration
- (M) – Indicates a URL that contains the search term and the URL itself must be edited manually

When you click any of the categories, such as Username, Email Address, or Domain Name, a lot of useful resources will appear on the screen, in the form of a sub-tree.
Searching for users, email addresses, IP addresses or social network details becomes super easy as you have all the tools available in one single interface. It's just like a giant OSINT bookmarks library.
For example, within IP Address, specifically through the Protected by Cloud Services section, you will find links to CloudFlare Watch and CloudFail.
The same happens with other popular categories such as Email Address — Breach Data you will find many links to useful resources such as Have I been pwned? or DeHashed.
We've written about port scanners before, also about Nmap commands the last time, but this framework offers a lot of alternatives for finding ways to scan ports, such as:
- Shodan
- Urlscan.io
- EyeScans.io
- Mr.Looquer
- ZoomEye
Social network data exploration is also available by offering access to a lot of tools including LinkedIn, Reddit, Google+, Twitter and Facebook.
Linkedin isn't as exploited a network when compared to Facebook or Twitter, and even in this case, this framework offers great tools like LinkedInt, ScrapedIn and the IntelTechniques LinkedIn tool.
When it comes to Domain and DNS History, you'll find a few tools in the PassiveDNS section, including our own SecurityTrails toolkit, Mnemonic, PTRarchive.com, and DNS Dumpster.
As you know, with SecurityTrails you're able to take a quick look into domain DNS history, along with useful information about IP addresses, historical IP records, WHOIS history, and correlate all that information in a single place.

Another interesting category that caught our attention was “Vulnerabilities,” found within the Domain Names category, which offers access to a lot of good vulnerability and top CVE databases, such as:
- Mage Scan
- Sn1per (T)
- ASafaWeb
- Zone-H.org
- XSSposed.org
Do you need to identify phone numbers? There are a lot of phone number tracking tools that allow you to identify an incoming call. These include:
- OpenCNAM
- HLR Lookup Portal ®
- Data24-7 ®
- Next Caller ®
- CallerIDService.com ®
- Mr. Number (M)
- Free Carrier Lookup
- Phone Validator
- ThatsThem
- CallerID Test
- Whocalld
You can even find a category dedicated to the Dark Web, classified in five subsections that include General Information, Dark Web Clients, Content Discovery, TOR Search and Directories.
Accessing Dark Web tools and popular sites using .onion with features like these only takes seconds:
- DeepDotWeb
- I2P Anonymous Network (T)
- Tor Download (T)
- Onion Investigator
- docker-onion-nmap (T)
- Hunchly Hidden Services Report
- Onioff
- Tor Scan
- OnionScan
- Ahmia
- OnionLink

Another useful category we found was one called “Code Search,” which will give you access to sites that are specialized in code search.
These sites can be used to search for lines of code on past and present projects, companies, online repositories and much more. Some of the best we found include:
- PublicWWW
- Github-Dorks (T)
- Gitrob (T)
- NerdyData
- Searchcode

There is also a great section called “Archives,” which features links to popular sites and tools for retrieving historical information. The list includes popular options like:
- Waybackpack (T)
- Browsershots
- Bounce
- PDFmyURL
- Wayback Machine Chrome Extension
- Common Crawl
- Wayback Machine – Beta Search
- Screenshots.com
- UK Web Archive
- Textfiles.com
- Cached Pages
- Cached View
- WebCite
- Archive.is
In that same category, a section called “Data Leaks” offers interesting leaks from critical data extracted and published on popular websites such as WikiLeaks or Cryptome.
On the lowest part of the OSINT Framework resource tree, you will find other tools that can help your investigation when no individuals are involved, such as OpSec, code analysis, malware identification, metadata analysis, etc. These include popular tools like:
- ExifTool
- FOCA (T)
- Metagoofil (T)
- Sandbox
- Pikker.ee Cuckoo Sandbox
- Joe File Analyzer
- Ether
- MalwareViz
- Hybrid Analysis
- Malwr
- VirusTotal
Final thoughts
As you can see by browsing the OSINT Framework website, there are almost unlimited ways to get data about any target you're investigating.
Plus, this framework can be used as a good cybersecurity checklist to see what areas you have left to explore while analyzing any individual or company.
Here at SecurityTrails we've built one of the most trusted and biggest OSINT tools for infosec professionals, one that allows you to grab valuable information about IP addresses, DNS, domains and SSL certificates from one single place.
Book a SurfaceBrowser demo with our sales team, or start grabbing a free API account to integrate our powerful OSINT features with your own apps.




