Enabling or disabling security and analysis features for public repositories
You can manage a subset of security and analysis features for public repositories. Other features are permanently enabled, including dependency graph and secret scanning.
- On GitHub, navigate to the main page of the repository.
- Under your repository name, click
Settings.

- In the left sidebar, click Security & analysis.
- Under "Configure security and analysis features", to the right of the feature, click Disable or Enable.

Enabling or disabling security and analysis features for private repositories
You can manage the security and analysis features for your private or internal repository. If your organization belongs to an enterprise with a license for GitHub Advanced Security then extra options are available. For more information, see "About GitHub Advanced Security."
If you enable security and analysis features, GitHub performs read-only analysis on your repository. For more information, see "About GitHub's use of your data."
-
On GitHub, navigate to the main page of the repository.
-
Under your repository name, click Settings.

-
In the left sidebar, click Security & analysis.

-
Under "Configure security and analysis features", to the right of the feature, click Disable or Enable. The control for "GitHub Advanced Security" is disabled if your enterprise has no available licenses for Advanced Security.

Note: If you disable GitHub Advanced Security, dependency review, secret scanning and code scanning are disabled. Any workflows, SARIF uploads, or API calls for code scanning will fail.
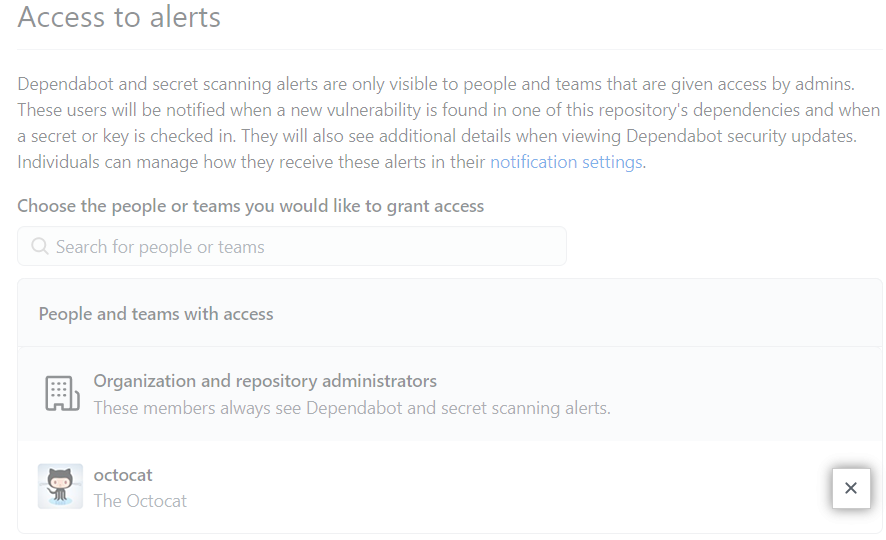
Granting access to security alerts
After you enable Dependabot or secret scanning alerts for a repository in an organization, organization owners and repository administrators can view the alerts by default. You can give additional teams and people access to the alerts for a repository.
Organization owners and repository administrators can only grant access to view security alerts, such as secret scanning alerts, to people or teams who have write access to the repo.
-
On GitHub, navigate to the main page of the repository.
-
Under your repository name, click Settings.

-
In the left sidebar, click Security & analysis.

-
Under "Access to alerts", in the search field, start typing the name of the person or team you'd like to find, then click a name in the list of matches.

-
Click Save changes.

Removing access to security alerts
- On GitHub, navigate to the main page of the repository.
- Under your repository name, click
Settings.

- In the left sidebar, click Security & analysis.

- Under "Access to alerts", to the right of the person or team whose access you'd like to remove, click .