About SAML single sign-on for enterprise accounts
SAML single sign-on (SSO) gives organization owners and enterprise owners on GitHub a way to control and secure access to organization resources like repositories, issues, and pull requests. For more information, see "About identity and access management with SAML single sign-on."
Enterprise owners can enable SAML SSO and centralized authentication through a SAML IdP across all organizations owned by an enterprise account. After you enable SAML SSO for your enterprise account, SAML SSO is enforced for all organizations owned by your enterprise account. All members will be required to authenticate using SAML SSO to gain access to the organizations where they are a member, and enterprise owners will be required to authenticate using SAML SSO when accessing an enterprise account.
To access each organization's resources on GitHub, the member must have an active SAML session in their browser. To access each organization's protected resources using the API and Git, the member must use a personal access token or SSH key that the member has authorized for use with the organization. Enterprise owners can view and revoke a member's linked identity, active sessions, or authorized credentials at any time. For more information, see "Viewing and managing a user's SAML access to your enterprise account."
We offer limited support for all identity providers that implement the SAML 2.0 standard. We officially support these identity providers that have been internally tested:
- Active Directory Federation Services (AD FS)
- Azure Active Directory (Azure AD)
- Okta
- OneLogin
- PingOne
- Shibboleth
Provisioning and deprovisioning user access with SCIM is not available for enterprise accounts.
Enforcing SAML single-sign on for organizations in your enterprise account
Notes:
- When you enable SAML SSO for your enterprise, the enterprise configuration will override any existing organization-level SAML configurations.
- When you enforce SAML SSO for an organization, GitHub removes any members of the organization that have not authenticated successfully with your SAML IdP. When you require SAML SSO for your enterprise, GitHub does not remove members of the enterprise that have not authenticated successfully with your SAML IdP. The next time a member accesses the enterprise's resources, the member must authenticate with your SAML IdP.
For more detailed information about how to enable SAML using Okta, see "Configuring SAML single sign-on for your enterprise account using Okta."
-
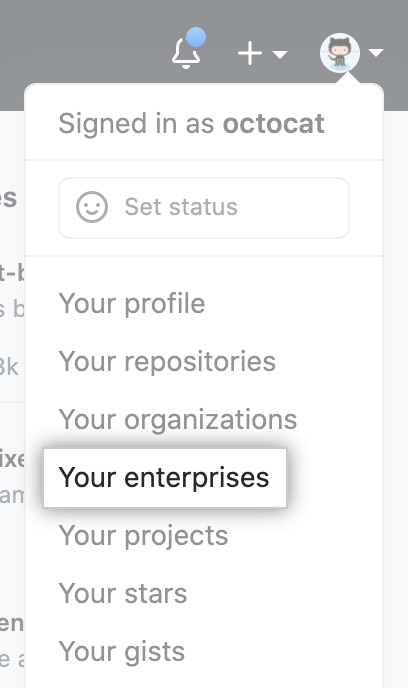
In the top-right corner of GitHub, click your profile photo, then click Your enterprises.
-
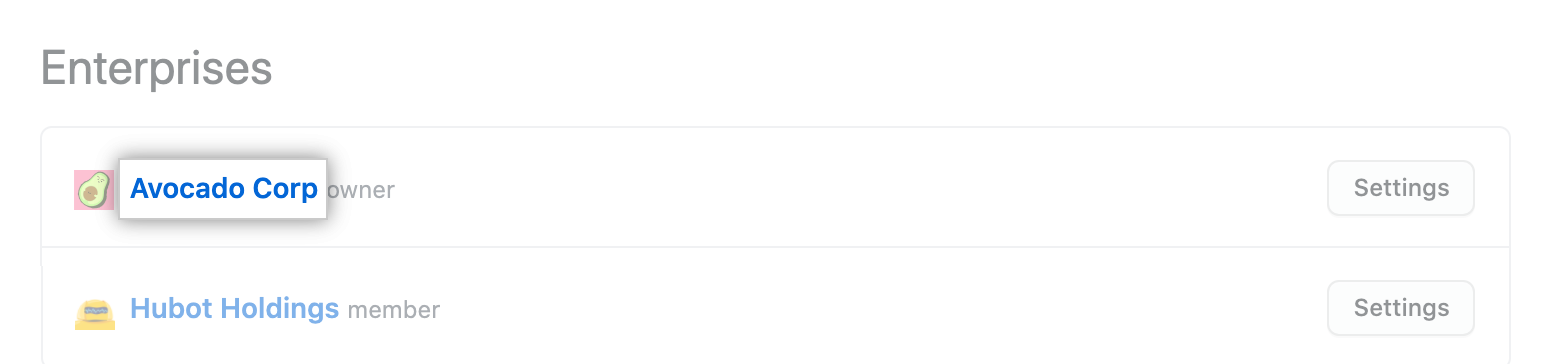
In the list of enterprises, click the enterprise you want to view.
-
In the enterprise account sidebar, click Settings.

-
In the left sidebar, click Security.

-
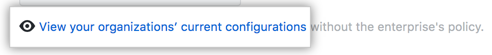
Optionally, to view the current configuration for all organizations in the enterprise account before you change the setting, click View your organizations' current configurations.
-
Under "SAML single sign-on", select Require SAML authentication.

-
In the Sign on URL field, type the HTTPS endpoint of your IdP for single sign-on requests. This value is available in your IdP configuration.

-
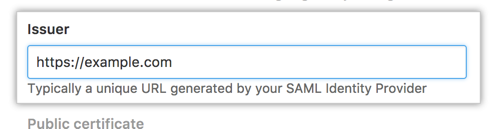
Optionally, in the Issuer field, type your SAML issuer URL to verify the authenticity of sent messages.
-
Under Public Certificate, paste a certificate to verify SAML responses.
-
To verify the integrity of the requests from your SAML issuer, click . Then in the "Signature Method" and "Digest Method" drop-downs, choose the hashing algorithm used by your SAML issuer.

-
Before enabling SAML SSO for your enterprise, click Test SAML configuration to ensure that the information you've entered is correct.

-
Click Save.