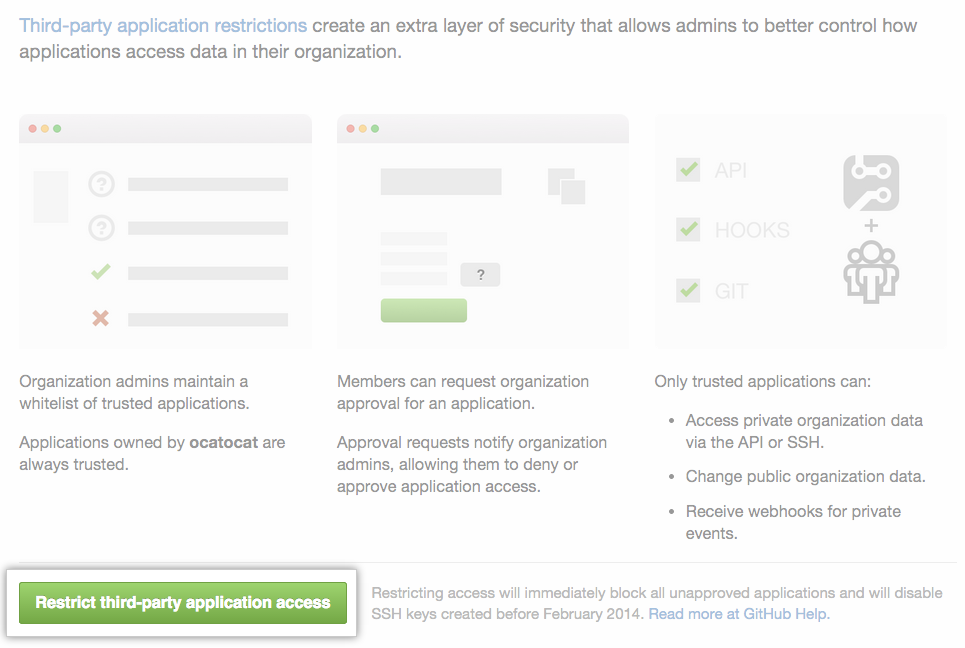
When you create a new organization, OAuth App access restrictions are enabled by default. Organization owners can disable OAuth App access restrictions at any time.
Warnings:
- Enabling OAuth App access restrictions will revoke organization access for all previously authorized OAuth Apps and SSH keys. For more information, see "About OAuth App access restrictions."
- Once you've set up OAuth App access restrictions, make sure to re-authorize any OAuth App that require access to the organization's private data on an ongoing basis. All organization members will need to create new SSH keys, and the organization will need to create new deploy keys as needed.
- When OAuth App access restrictions are enabled, applications can use an OAuth token to access information about GitHub Marketplace transactions.
-
In the top right corner of GitHub, click your profile photo, then click Your organizations.

-
Next to the organization, click Settings.

-
In the Settings sidebar, click Third-party access.
-
Under "Third-party application access policy," click Setup application access restrictions.

-
After you review the information about third-party access restrictions, click Restrict third-party application access.