SQLPlus: Reading traces and incident files

@tracefile_read_last_by_mask filemask [regexp] [ignore_regexp]
– finds last trace by filemask and filters rows by regexp and filters out rows by ignore_regexp:

@tracefile_read_last_by_mask filemask [regexp] [ignore_regexp]
– finds last trace by filemask and filters rows by regexp and filters out rows by ignore_regexp:

We describe the implementation of a custom Domain Name System (DNS) by using C socket programming for network communication, together with SQLite3 database for the storage of Internet Protocol (IP) for Uniform Resource Locator (URL). Then we provide a performance analysis of our implementation. Our code is available publicly [1].

On implementing streaming algorithms, counting of events often occurs, where an event means something like a packet arrival or a connection establishment. Since the number of events is large, the available memory can become a bottleneck: an ordinary -bit counter allows to take into account no more than
events.
One way to handle a larger range of values using the same amount of memory would be approximate counting. This article provides an overview of the well-known Morris algorithm and some generalizations of it.
Another way to reduce the number of bits required for counting mass events is to use decay. We discuss such an approach here [3], and we are going to publish another blog post on this particular topic shortly.
In the beginning of this article, we analyse one straightforward probabilistic calculation algorithm and highlight its shortcomings (Section 2). Then (Section 3), we describe the algorithm proposed by Robert Morris in 1978 and indicate its most essential properties and advantages. For most non-trivial formulas and statements, the text contains our proofs, the demanding reader can find them in the inserts. In the following three sections, we outline valuable extensions of the classic algorithm: you can learn what Morris's counters and exponential decay have in common, how to improve the accuracy by sacrificing the maximum value, and how to handle weighted events efficiently.

The new issue of Data Science Digest is here! Hop to learn about the latest news, articles, tutorials, research papers, and event materials on DataScience, AI, ML, and BigData. All sections are prioritized for your convenience. Enjoy!

Dynamic programming is applied to solve optimization problems. In optimization, we try to find out the maximum or minimum solution of something. It will find out the optimal solution to any problem if that solution exists. If the solution does not exist, dynamic programming is not able to get the optimal solution.
Optimization problems are the ones that require either lowest or highest possible results. We attempt to discover all the possible solutions in dynamic programming and then choose the best optimal solution. Dynamic programming problems are solved by utilizing the recursive formulas though we will not use a recursion of programming the procedures are recursive. Dynamic programming pursues the rule of optimality.
A dynamic programming working involves around following significant steps:

Asymptotic notations are used to represent the complexity or running time of an algorithm. It is a technique of defining the upper and lower limits of the run-time performance of an algorithm. We can analyze the runtime performance of an algorithm with the help of asymptotic notations. Asymptotic notations are also used to describe the approximate running time of an algorithm.
Types of Asymptotic Notations
Following are the different types of asymptotic notations:
What this article is about
In this article, we will talk about multithreading in the backend.
• how it is implemented
• how is it used
• what can be done
• what we invented ourselves
All these questions are relevant only if you develop something for the server side - modify the Server SDK code, write your own plugin, or even start some server application from scratch.

In this topic, I will tell you how to dynamically parse and deserialize only part of the whole JSON document. We will create an implementation for .NET Core with C# as a language.
For example, we have the next JSON as a data source for the report. Notice that we will get this JSON in the runtime and at the compile step we don't know the structure of this document. And what if you need to select only several fields for processing?
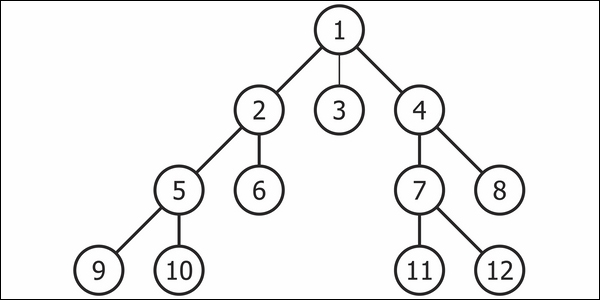
A graph is a kind of data structure that includes a set of vertices and edges. Graph traversing means a visit to each vertex of the graph precisely. The graph traversing is used to determine the order in which vertices are being visited throughout the search process. A graph traversing searches for the edges that will be used in the search operation without establishing loops. This means that using graph traversal, we will go to all the vertices of the graph without going into a looping path.
There are two kinds of graph traversal methods.

Hi, My name is Alex and I am a DevOps engineer at Altenar. “No Windows, no problems.” - that is the answer I got by asking a guru of Ansible "How do you manage Windows?" on one of the local Ansible meetups. Although we have been running a modern stack (k8s, helm, .net core, etc) in production for about two years, that’s not how it has always been.

Stack
Stack is a linear data structure. In stack, data access is limited. It follows the rule of insertion and deletion of data. Stack is a collection of only similar data types. Elements in the stack are arranged sequentially. It follows the LIFO principle which is the last-in and first-out rule.
Example
To understand this concept, let us take an example of arranging coins. If we start placing coins one after the other in such a way that the first coin will be placed first at the bottom and the next coin will come on above the first coin and so on. Now if we want to remove coins, then the topmost coin which is the third coin will be removed first. So in this way, the last coin will be removed first according to the LIFO principle.

PVS-Studio user support often receives clients' suggestions on product improvement. We are happy to implement many of them. Recently one of the users suggested refining the automatic notification utility for developers (Blame Notifier). They asked us to make Blame Notifier extract the date/the code revision to which the analyzer issued a message using blame information from the version control system. This feature allowed us to expand the utility capabilities, which we'll discuss in this article.

The previous year has been very distressing for businesses and employees. Though, software development didn’t get so much affected and is still thriving. While tech expansion is continuing, Java development is also going under significant transformation.
The arrival of new concepts and technologies has imposed a question mark on the potential of Java developers. From wearable applications to AI solutions, Java usage is a matter of concern for peers.
Moreover, it is high time that developers enhance their skills as to the changing demands of the industry. If you are a Java developer, surely you too would be wondering what I am talking about what things you should learn.

Link to Part 1.
A SimpleGAS is a set of tutorials for entry-level Unreal Engine enthusiasts who wants to leverage the power of the Gameplay Ability System in their prototypes. While there are great tutorials and GitHub repositories which cover the topic of GAS in more depth, this tutorial is requiring a minimum C++ setup and showcases working examples built entirely using Blueprints. This tutorial is for those who are new to Unreal Engine gameplay/multiplayer development or simply need an easy headstart before diving into more sophisticated GAS-related content.
Today we finish what we started in Part 1 and make replicated grenade projectiles using Gameplay Ability System...

"How much longer are you going to build it?" - a phrase that every developer has uttered at least once in the middle of the night. Yes, a build can be long and there is no escaping it. One does not simply redistribute the whole thing among 100+ cores, instead of some pathetic 8-12 ones. Or is it possible?

We are increasingly aware of the importance of our personal data. Primarily due to numerous data leaks and the fact of numerous sales of personal information on the black market. Yes, huge corporations like Apple or Samsung prioritize the preservation of sensitive user data. However, they find it difficult to store and use them at the same time. That is why blockchain technology is the perfect tool for solving the online privacy problem.
There are constant news in the media about the problem of personal privacy, which is represented by constant data leaks and the general technological illiteracy of the world population. In the Pew study, nearly 80% of respondents said they are very concerned about how companies are using the data they collect. In MState's study, 24% of respondents stopped using certain apps due to privacy concerns.
Today, an increasing number of people are actively protecting their data by refusing the services of companies and applications that use personal data. This is why Apple, Lyft, Dropbox, and Adobe have started taking a consumer-centric approach to data privacy. Consumers' understanding that their personal data is a commodity is increasing.
Free TON is a prime example of a secure blockchain. This blockchain has some of the best features compared to Ethereum, Binance Smart Chain, and Stellar. Data security directly depends on the use of blockchain. Each of the above blockchains provides a different level of data protection. Ethereum is the most popular blockchain, but Free TON may soon overtake it. This blockchain is just over a year old, and its capabilities exceed those of all other blockchains.
FTPS - is FTP with SSL layer, please don't mess it with SFTP. FTPS uses regular FTP protocol underneath, but all commands and data is encrypted using SSL. So mechanism of work is pretty same as in HTTPS: old protocol encapsulated in security layer. But that's breaks a lot of traditional FTP clients you are used to.
So here is 2 dead simple solutions I've tested with many FTPS servers, which setup could be much more correct then it actualy was. You can encounter FTPS servers configured in 2 ways with ports 20 + 21 and 989 + 990 used.
Filezilla
Filezilla is a GUI client available for both linux and windows. It has pretty specific interface. It can correctly handle wrong certificates, unusual ports and so on. Can be downloaded here. Just enter host, username, password and port(only if needed) and press Connect.
Mounting FTPS under linux
There is a an utililty called curlftpfs. It works under linux/*bsd and allows to mount remote FTPS(S) dir to you local directory. So in the simpliest ways on the ubuntu/debian it will look like:
sudo apt install curlftpfs
mkdir /tmp/ftp-mount
curlftpfscurlftpfs -o ssl ftp://USERNAME:PASSWORD@HOSTNAME:21/ /tmp/ftp-mount
If server you connecting to has wrong or outdated SSL certificate you can try:
curlftpfs -o ssl,no_verify_peer,no_verify_hostname ftp://USERNAME:PASSWORD@HOSTNAME:21/ /tmp/ftp-mount
If you need to change port from 21 to something else, remember, you can change port only in connection string, maybe via .netrc, but NOT with curlftpfs ftp_port option.
If you know a solution that allows to mount ftps folders under Windows, please mention it in comments.

Smoothly the era of mesh-networks is upon us. At the very least, the term is appearing more and more often in the information sphere. What attracts the attention of networkers? Let's try to understand the question, taking Yggdrasil network as an example as one of the most promising prototypes. The article is intended for a wide range of readers.

Many of us spend time in specialized telegram groups. The power over communication here belongs to random people with their own shortcomings. Conflict and abuse occurs regularly. Is there another way to keep order so that scam spam doesn't flourish and no one has total control over group members?
In my case, these thoughts led to the development and testing of a system that can be connected to your Telegram today.

Introduction
It was 1989 when 2 editors of Inc. magazine, George Gendron and Bo Burlingham made the nervous drive to Palo Alto, California. Not long beforehand they’d decided on who to name as Inc.’s Entrepreneur of the Decade, and finally, they would get a chance to interview him.
As they entered the offices of NeXT, their interviewee approached them. In his trademark jeans and turtleneck sweater, Steve Jobs led them up the stairs to his office and the interview commenced.
Securing an interview with Steve Jobs was rare, even in 1989. And, wanting to make the most of their time, the editors got straight to the point with their very first question:
“Where do great products come from?”
After a slight pause, and a shuffle in his chair, Jobs replied:
“I think really great products come from melding two points of view; the technology point of view and the customer point of view. You need both. You can't just ask customers what they want and then try to give that to them. By the time you get it built, they'll want something new.”
Silence overshadowed the room. Three decades later, and this powerful answer Jobs gave is something that still isn’t often internalized in companies.
Collecting user feedback is incredibly important. As you’ll see examples of later in this article, launching surveys, asking onboarding questions, and conducting customer interviews are all vital tools for improving your product.
But the true lesson that Steve Jobs gave all this time ago was that user feedback isn’t as simple as asking what users want, or what they think about your product, and making those changes. You have to dive much deeper.