Big Time Crooks

When an online scam becomes too successful, the results can be farcical.
In the movie Small Time Crooks, Woody Allen leads an inept gang of would-be robbers who rent a store next to a bank. They plan to tunnel into the vault. As a cover, Allen’s girlfriend (played by Tracey Ullman) sets up a cookie business in the store. Ullman’s business takes off, and to maintain the cover the gang must set up production facilities, hire staff, find distributors, and so on.
Why is this relevant? Well, rewind to 2002. The internet had already taken off in a big way and people were pouring online as new opportunities exploded into the public consciousness. Also exploding was cybercrime, as the internet presented a new breed of tech savvy crooks with their own set of opportunities. For one gang, an Allenesque adventure was about to begin.
Humble Beginnings
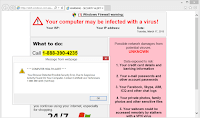
How many times have you browsed a web page that suddenly throws up an alarming warning that your computer is infected and the only thing that can save you is to immediately buy a special program or call a special number? If you’re up to date with system patches and use a reputable anti-virus solution, you’re rarely in danger from such sites these days.
It was not always so.
For millions of internet users back in the day, who were running without protection, the apparent authority of such “scareware” sites made them act. They downloaded free “anti-virus” software that infected them with real malware, they parted with real cash, and many also paid again to have their computers cleaned by professionals.
 Look through the history of scareware, and one company repeatedly appears: Innovative Marketing Inc (to give it the name used in US Federal Trade Commission paperwork but also known by a wide
Look through the history of scareware, and one company repeatedly appears: Innovative Marketing Inc (to give it the name used in US Federal Trade Commission paperwork but also known by a wide
range of other names). Innovative was registered in Belize in 2002. Despite the appearance of being a legitimate business, its initial products were dodgy: pirated music, porn and illicit Viagra, along with sales of “grey” versions of real anti-virus products.
After Symantec and McAfee both put pressure on the company to stop those software sales in 2003, Innovative tried to write its own. The resulting Computershield wasn’t effective as anti-virus protection, but the company sold it anyway as a defence against the MyDoom worm. Innovative aggressively marketed its new product, and according to press reports, it was soon raking in $1 million per month. As the threat from MyDoom receded, so too did profits.
The company initially turned to adware as a new revenue source. This enabled so-called “affiliates” to use malicious web sites to silently install the adware on vulnerable Windows computers. Getting victims to visit those sites was achieved by placing what looked like legitimate adverts on real sites. Click them, and you became infected. The affiliates then pocketed a fee of 10 cents per infection, but it’s through that Innovative made between $2 and $5 from sales of the advertised products.
Meanwhile, development of completely fake anti-virus software snowballed at the company’s Kiev office. A classic example is “XP Antivirus 2008”, though it also went by a large number of pseudonyms and evolved through many versions. A video of it trashing an XP machine can be found here. Its other major names include Winfixer, WinAntivirus, Drivecleaner, and SystemDoctor.
In many ways, Innovative’s scareware was, well, innovative. It disabled any legitimate protection and told you the machine was heavily infected, even going to the trouble of creating fake blue screens of death. At the time, some antivirus companies had trouble keeping up with the rate of development.
Attempts to access Windows internet or security settings were blocked. The only way of “cleaning” the machine was to register the software and pay the fee. Millions of people did just that. The FTC estimates that between 2004 and 2008, the company and its subsidiaries raked in $163 million.
In 2008, a hacker with the handle NeoN found a database belonging to one of the developers, revealing that in a single week one affiliate made over $158,000 from infections.
The Problem of Success
Initially, Innovative used banks in Canada to process the credit card transactions of its victims, but problems quickly mounted as disgruntled cardholders began raising chargebacks. These are claims made to credit card companies about shoddy goods or services.
With Canadian banks beginning to refuse Innovative’s business, it created subsidiary companies to hide its true identity, and approached the Bank of Kuwait and Bahrain. Trouble followed, and in 2005 this bank also stopped handling Innovative’s business due to the high number of chargebacks. Eventually, the company found a Singaporean bank called DBS Bank to handle the mounting backlog of credit card transactions.
The only solution to the chargeback problem was to keep customers happy. So, in true Allenesque style, Innovative began to invest in call centres to help customers through their difficulties. It quickly opened facilities in Ukraine, India and the USA. Operatives would talk the customers through the steps needed for the software to miraculously declare their systems free of malware. It seems that enough customers were satisfied to allow the company to keep on raking in the cash.
But people did complain, not to the company but to the authorities. The FTC received over 3,000 complaints in all and launched an investigation. Marc D’Souza has been convicted of his role in the company and ordered to pay £8.2 million, along with his father who received some of the money. The case of Kristy Ross for her part in the scam is still going through the US courts, with lawyers arguing that she was merely an employee.
Several others, including Shaileshkumar “Sam” Jain and Bjorn Daniel Sundin, are still at large, and have had a $163 million judgement entered against them in their absence. Jain and Sundin remain on the FBI’s Most Wanted Cyber Criminal list with rewards for their arrests totalling $40,000.
An Evergreen Scam
Scareware is a business model that rewards creativity while skirting the bounds of legality. Unlike ransomware, where criminal gangs must cover their tracks with a web of bank accounts and Bitcoin wallets, scareware can operate quite openly from countries with under-developed law enforcement and rife corruption. However, the gap between scareware and ransomware is rapidly closing.
 Take the case of Latvian hacker Peteris Sahurovs, AKA “Piotrek” AKA “Sagade”. He was arrested on an international arrest warrant in Latvia in 2011 for his part in a scareware scam, but he fled to Poland where he was subsequently detained in 2016.
Take the case of Latvian hacker Peteris Sahurovs, AKA “Piotrek” AKA “Sagade”. He was arrested on an international arrest warrant in Latvia in 2011 for his part in a scareware scam, but he fled to Poland where he was subsequently detained in 2016.
He was extradited to the US and pled guilty in February this year to making $150,000 – $200,000. US authorities claim the total made by Sahurovs’ gang was closer to $2 million. He’s due to be sentenced in June.
According to the Department of Justice, the Sahurovs gang set up a fake advertising agency that claimed to represent a US hotel chain. Once adverts were purchased on the Minneapolis Star Tribune’s website, they were quickly swapped out for ones that infected vulnerable visitors with their malware. This made computers freeze and produce pop-ups explaining that victims needed to purchase special antivirus software to restore proper functionality. This case is interesting as it shows a clear cross over from scareware to ransomware. All data on the machines was scrambled until the software was purchased.
The level of sophistication and ingenuity displayed by scareware gangs is increasing, as is their boldness. You have probably been called by someone from India claiming to be from Microsoft, expressing concern that your computer is badly infected and offering to fix it. Or they may have posed as someone from your phone company telling you that they need to take certain steps to restore your internet connection to full health. There are many variations on the theme. Generally, they want you to download software that confirms their diagnosis. Once done, you must pay them to fix the problem. This has led to a plethora of amusing examples of playing the attackers at their own game.
It’s easy to see the people who call you as victims of poverty with no choice but to scam, but string them along for a while and the insults soon fly. They know exactly what they’re doing, and from the background chatter on such calls, so do hundreds of others. Scareware in all its forms is a crime that continues to bring in a lot of money for its perpetrators and will remain a threat for years to come.







































